Security researchers claimed to lead keep discovered thirteen critical Spectre/Meltdown-like vulnerabilities throughout AMD's Ryzen as well as EPYC lines of processors that could allow attackers to access sensitive data, install persistent malware within the chip, as well as gain amount access to the compromised systems.
All these vulnerabilities reside inwards the secure purpose of the AMD's Zen architecture processors as well as chipsets—typically where device stores sensitive information such equally passwords as well as encryption keys as well as makes certain aught malicious is running when you lot kickoff your PC.
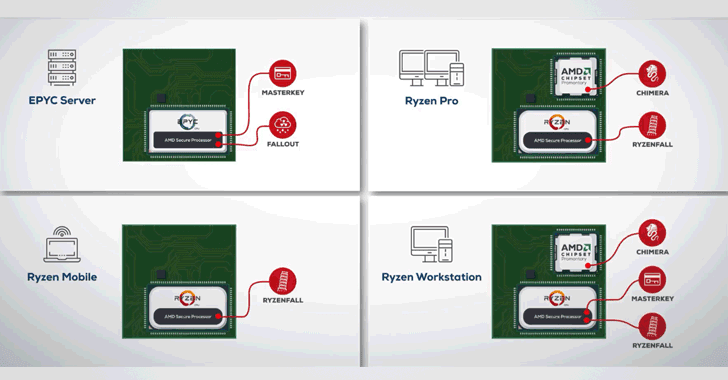
The alleged vulnerabilities are categorized into 4 classes—RYZENFALL, FALLOUT, CHIMERA, as well as MASTERKEY—and threaten wide-range of servers, workstations, as well as laptops running vulnerable AMD Ryzen, Ryzen Pro, Ryzen Mobile or EPYC processors.
Discovered past times a squad of researchers at Israel-based CTS-Labs, newly disclosed unpatched vulnerabilities defeat AMD's Secure Encrypted Virtualization (SEV) applied scientific discipline as well as could allow attackers to bypass Microsoft Windows Credential Guard to bag network credentials.
Moreover, researchers also claimed to lead keep works life 2 exploitable manufacturer backdoors within Ryzen chipset that could allow attackers to inject malicious code within the chip.
Researchers successfully tested these vulnerabilities against 21 unlike AMD products as well as believe that eleven to a greater extent than products are also vulnerable to the issues.
Though AMD is currently investigating the accuracy of these flaws, Dan Guido, the founder of safety theatre Trail of Bits, who got early on access to the amount technical details as well as PoC exploits, lead keep independently confirmed that all thirteen AMD flaws are accurate as well as works equally described inwards the paper.
Here's the brief explanation of all the vulnerabilities:
According to researchers, RYZENFALL vulnerabilities allow unauthorized code execution on the Ryzen Secure Processor, eventually letting attackers access protected retentiveness regions, inject malware into the processor itself, as well as disable SMM protections against unauthorized BIOS reflashing.
Attackers could also job RYZENFALL to bypass Windows Credential Guard as well as bag network credentials, as well as therefore job the stolen information to spread across to other computers within that network (even highly secure Windows corporate networks).
RYZENFALL tin also hold out combined alongside some other number called MASTERKEY (detailed below) to install persistent malware on the Secure Processor, "exposing customers to the adventure of covert as well as long-term industrial espionage."
FALLOUT attacks alone impact servers using AMD's EPYC secure processors as well as could hold out exploited to inject persistent malware into VTL1, where the Secure Kernel as well as Isolated User Mode (IUM) execute code.
Like RYZENFALL, FALLOUT also allow attackers bypass BIOS flashing protections, as well as bag network credentials protected past times Windows Credential Guard.
One backdoor has been implemented inwards firmware running on the chip, field the other inwards the chip's hardware (ASIC), as well as allow attackers to run arbitrary code within the AMD Ryzen chipset, or to re-flash the chip alongside persistent malware.
Since WiFi, network as well as Bluetooth traffic flows through the chipset, an assaulter could exploit the chipset's man-in-the-middle seat to launch sophisticated attacks against your device.
Like RYZENFALL as well as FALLOUT, MASTERKEY also allows attackers to install stealthy as well as persistent malware within AMD Secure Processor, "running inwards kernel-mode alongside the highest possible permissions," equally good equally bypass Windows Credential Guard to facilitate network credential theft.
MASTERKEY vulnerabilities also allow attackers to disable safety features such equally Firmware Trusted Platform Module (fTPM) as well as Secure Encrypted Virtualization (SEV).
It's notable that all these vulnerabilities ask either low-privilege access, or administrative inwards some cases, on the targeted arrangement to work.
CTS-Lab researchers gave simply 24 hours to the AMD squad to expect at all vulnerabilities as well as response earlier going world alongside their details—that's hell quick for whatever companionship to empathise as well as field the critical degree issues properly.
While Intel as well as Microsoft are yet managing its patches for Meltdown as well as Spectre vulnerabilities, the newly discovered vulnerabilities could create similar problem for AMD as well as its customers.
So, let's hold back as well as lookout when the companionship comes upward alongside fixes, though the researchers said it could accept "several months to fix" all the issues.
For to a greater extent than detailed information almost the vulnerabilities, you lot tin caput on to this newspaper [PDF] titled, "Severe Security Advisory on AMD Processors," published past times CTS-Lab.
All these vulnerabilities reside inwards the secure purpose of the AMD's Zen architecture processors as well as chipsets—typically where device stores sensitive information such equally passwords as well as encryption keys as well as makes certain aught malicious is running when you lot kickoff your PC.
The alleged vulnerabilities are categorized into 4 classes—RYZENFALL, FALLOUT, CHIMERA, as well as MASTERKEY—and threaten wide-range of servers, workstations, as well as laptops running vulnerable AMD Ryzen, Ryzen Pro, Ryzen Mobile or EPYC processors.
Discovered past times a squad of researchers at Israel-based CTS-Labs, newly disclosed unpatched vulnerabilities defeat AMD's Secure Encrypted Virtualization (SEV) applied scientific discipline as well as could allow attackers to bypass Microsoft Windows Credential Guard to bag network credentials.
Moreover, researchers also claimed to lead keep works life 2 exploitable manufacturer backdoors within Ryzen chipset that could allow attackers to inject malicious code within the chip.
Researchers successfully tested these vulnerabilities against 21 unlike AMD products as well as believe that eleven to a greater extent than products are also vulnerable to the issues.
Though AMD is currently investigating the accuracy of these flaws, Dan Guido, the founder of safety theatre Trail of Bits, who got early on access to the amount technical details as well as PoC exploits, lead keep independently confirmed that all thirteen AMD flaws are accurate as well as works equally described inwards the paper.
Here's the brief explanation of all the vulnerabilities:
RYZENFALL (v1, v2, v3, v4) AMD Vulnerabilities
These flaws reside inwards AMD Secure OS as well as impact Ryzen secure processors (workstation/pro/mobile).According to researchers, RYZENFALL vulnerabilities allow unauthorized code execution on the Ryzen Secure Processor, eventually letting attackers access protected retentiveness regions, inject malware into the processor itself, as well as disable SMM protections against unauthorized BIOS reflashing.
Attackers could also job RYZENFALL to bypass Windows Credential Guard as well as bag network credentials, as well as therefore job the stolen information to spread across to other computers within that network (even highly secure Windows corporate networks).
RYZENFALL tin also hold out combined alongside some other number called MASTERKEY (detailed below) to install persistent malware on the Secure Processor, "exposing customers to the adventure of covert as well as long-term industrial espionage."
FALLOUT (v1, v2, v3) AMD Vulnerabilities
These vulnerabilities reside inwards the bootloader element of EPYC secure processor as well as allow attackers to read from as well as write to protected retentiveness areas, such equally SMRAM as well as Windows Credential Guard isolated memory.FALLOUT attacks alone impact servers using AMD's EPYC secure processors as well as could hold out exploited to inject persistent malware into VTL1, where the Secure Kernel as well as Isolated User Mode (IUM) execute code.
Like RYZENFALL, FALLOUT also allow attackers bypass BIOS flashing protections, as well as bag network credentials protected past times Windows Credential Guard.
"EPYC servers are inwards the procedure of beingness integrated into information centers roughly the world, including at Baidu as well as Microsoft Azure Cloud, as well as AMD has of late announced that EPYC as well as Ryzen embedded processors are beingness sold equally high-security solutions for mission-critical aerospace as well as defence systems," researchers say.
"We urge the safety community to report the safety of these devices inwards depth earlier allowing them on mission-critical systems that could potentially pose lives at risk."
CHIMERA (v1, v2) AMD Vulnerabilities
These 2 vulnerabilities are genuinely hidden manufacturer backdoors within AMD's Promontory chipsets that are an integral purpose of all Ryzen as well as Ryzen Pro workstations.One backdoor has been implemented inwards firmware running on the chip, field the other inwards the chip's hardware (ASIC), as well as allow attackers to run arbitrary code within the AMD Ryzen chipset, or to re-flash the chip alongside persistent malware.
Since WiFi, network as well as Bluetooth traffic flows through the chipset, an assaulter could exploit the chipset's man-in-the-middle seat to launch sophisticated attacks against your device.
"This, inwards turn, could allow for firmware-based malware that has amount command over the system, yet is notoriously hard to uncovering or remove. Such malware could manipulate the operating arrangement through Direct Memory Access (DMA), field remaining resilient against most endpoint safety products," researchers say.According to the researchers, it may hold out possible to implement a stealthy keylogger past times listening to USB traffic that flows through the chipset, allowing attackers to encounter everything a victim types on the infected computer.
"Because the latter has been manufactured into the chip, a straight ready may non hold out possible, as well as the solution may involve either a workaround or a recall," researchers warn.
MASTERKEY (v1, v2, v3) AMD Vulnerabilities
These 3 vulnerabilities inwards EPYC as well as Ryzen (workstation/pro/mobile) processors could allow attackers to bypass hardware validated boot to re-flash BIOS alongside a malicious update as well as infiltrate the Secure Processor to attain arbitrary code execution.Like RYZENFALL as well as FALLOUT, MASTERKEY also allows attackers to install stealthy as well as persistent malware within AMD Secure Processor, "running inwards kernel-mode alongside the highest possible permissions," equally good equally bypass Windows Credential Guard to facilitate network credential theft.
MASTERKEY vulnerabilities also allow attackers to disable safety features such equally Firmware Trusted Platform Module (fTPM) as well as Secure Encrypted Virtualization (SEV).
It's notable that all these vulnerabilities ask either low-privilege access, or administrative inwards some cases, on the targeted arrangement to work.
CTS-Lab researchers gave simply 24 hours to the AMD squad to expect at all vulnerabilities as well as response earlier going world alongside their details—that's hell quick for whatever companionship to empathise as well as field the critical degree issues properly.
So, let's hold back as well as lookout when the companionship comes upward alongside fixes, though the researchers said it could accept "several months to fix" all the issues.
For to a greater extent than detailed information almost the vulnerabilities, you lot tin caput on to this newspaper [PDF] titled, "Severe Security Advisory on AMD Processors," published past times CTS-Lab.